| Siebel CRM Siebel Security Hardening Guide Siebel Innovation Pack 2015 E24815-01 |
|
 Previous |
 Next |
View PDF |
| Siebel CRM Siebel Security Hardening Guide Siebel Innovation Pack 2015 E24815-01 |
|
 Previous |
 Next |
View PDF |
This topic describes the recommended topologies for two different deployments of Siebel Business Applications:
A medium-scale, secure deployment of Siebel Business Applications with internal and external users
A large-scale, secure deployment of Siebel Business Applications with internal and external users where high-availability is crucial
Figure 3-3, "Network Configuration for a Medium-Scale Secure Deployment of Siebel Business Applications"shows the recommended placement of firewalls and related Siebel Enterprise Server components in a small or medium-scale Siebel Business Applications deployment with internal and external users. The Siebel network configuration for a medium-scale secure deployment is as follows:
Internet zone. External Siebel Web clients residing in the Internet zone access the Web server placed in the demilitarized zone through the external firewall.
Demilitarized zone. The Web server in this zone hosts a proxy server. The firewall keeps unauthorized users out of the protected network and the proxy server provides protection from various kinds of IP spoofing and routing attacks.
Intranet zone. The Siebel Web Server Extension (SWSE) is installed on the internal Web server in the intranet zone. The Siebel Gateway Name Server, Siebel Servers, and the third-party HTTP load balancer (if deployed) are also placed in the intranet zone.
Internal highly secure zone. This zone contains the Siebel database, Siebel File System, database server, and the authentication server (a Lightweight Directory Access Protocol (LDAP) server or Active Directory server). Limit access to this zone to authorized system administrators and database administrators.
Figure 3-3 Network Configuration for a Medium-Scale Secure Deployment of Siebel Business Applications
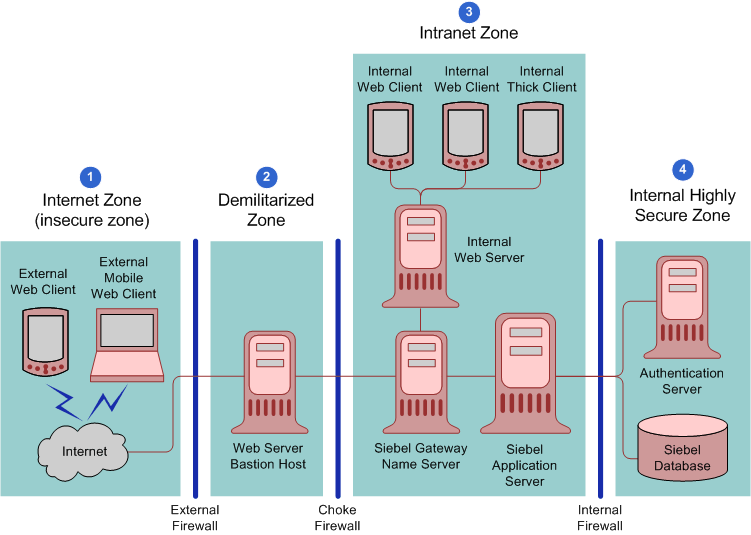
The network configuration approach illustrated in Figure 3-3 follows a defense-in-depth strategy by placing firewalls between the zones of control with only appropriate ports open. A secure channel is implemented using Transport Layer Security (TLS) between the external Web clients and the Web server to take care of security in the insecure Internet.
Figure 3-4, "Large Scale Highly Secure Deployment of Siebel Business Applications" shows the recommended placement of firewalls and related Siebel Enterprise Server components in a large-scale, secure Siebel Business Applications deployment with internal and external users. The Siebel network configuration for a large-scale secure deployment is as follows:
Internet zone. External Siebel Web clients residing in the Internet zone access the Web server placed in the demilitarized zone through the external firewall.
Demilitarized zone. A reverse-proxy server is included as a front end to the external Siebel Web clients to provide an extra layer of security in the demilitarized zone. The reverse-proxy server safeguards the Web server and the Siebel Servers. It acts as an intermediary to prevent direct connections from clients to Web servers, and it prevents the IP addresses of Web servers being revealed to the external world.
Intranet zone. The Web server, Siebel Gateway Name Server, and the Siebel Servers are placed inside the intranet zone. Siebel load balancing or third-party HTTP load balancing is implemented to distribute the processing load to multiple Siebel Servers.
Internal highly secure zone. The Siebel database, Siebel File System, database server, central authentication and authorization server, and the master authentication or authorization database server (LDAP or Active Directory server) are placed in the internal highly secure zone. They contain confidential data, with access limited to authorized system administrators and database administrators only.
Figure 3-4 Large Scale Highly Secure Deployment of Siebel Business Applications
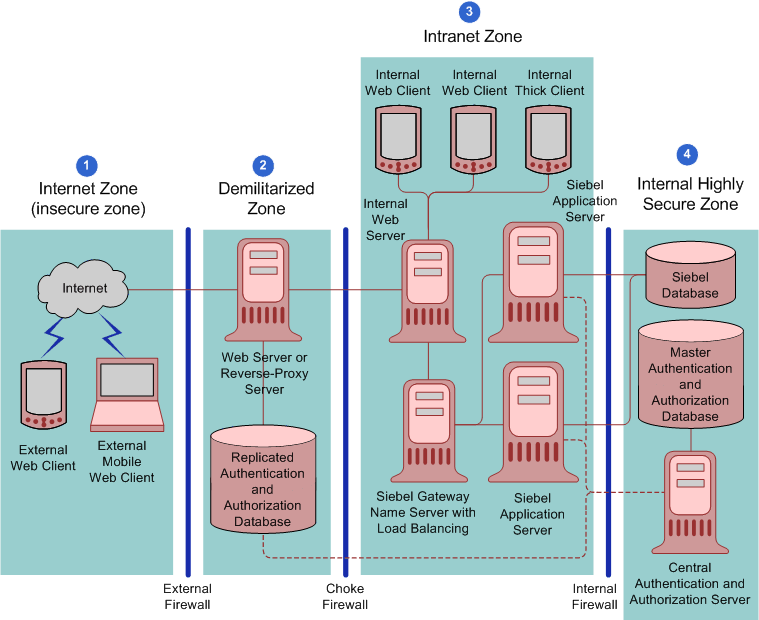
If you are using a centralized authentication and authorization system, then it is recommended to put a read-only replica of the authentication and authorization information in a database close to the reverse-proxy server in the demilitarized zone. (Determine whether or not to make a copy of the authentication database available in the demilitarized zone according to the sensitivity of your data.) Encrypt communications and information between the reverse-proxy server and the authentication database.
Using a replica database of the authentication information reduces the amount of traffic and firewall rules between the reverse-proxy server and the internal authentication and authorization servers. The centralized authentication system pushes the policies and rules to the replica database, and then the reverse-proxy server communicates with it. Although this type of configuration does not improve security, it improves application availability and performance. Availability is considered a part of security.